

HTTP protocol, the full name is HyperText Transfer Protocol, and the abbreviation letters of HTTP mean (HyperTest Transfer Protocol). It is essentially an application layer protocol for distributed and assisted information systems. It is also the World Wide Web we are familiar with. communication basis.
Related article:
HTTP was born not long ago. It was initiated by the European Organization for Nuclear Research (CERN) in 1989, and was discussed and coordinated by the World Wide Web Consortium (W3C) and the Internet Engineering Group (IETF). HTTP1.1 was jointly formulated by many parties as the first standard. A formally published standard.
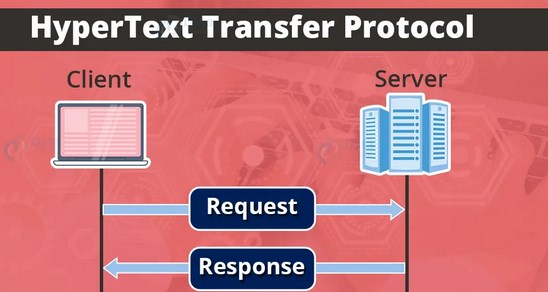
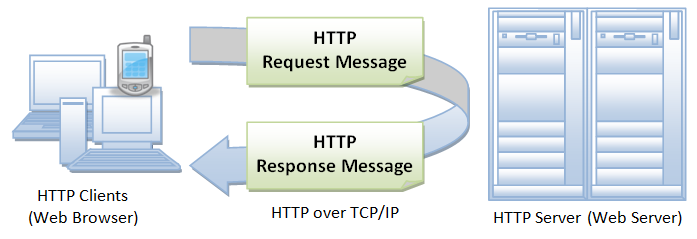
HTTP is essentially a standard for client (user) and server (website) to request and respond to data. Standard data interaction must meet this unified standard to facilitate the parsing and parsing of data by all parties. Use, and HTTP, as an application layer protocol built on top of the TCP communication layer, is equivalent to making relevant specifications for this type of data transmitted by TCP to achieve unification. For example, when we visit a certain website, the client will initiate an HTTP request to the server to the specified port (usually port 80). After receiving the marked HTTP request, the server needs to respond to the request, and the response The content is the HTML file (that is, the content seen on the web page) and image data stored on the server. These responses must also meet the HTTP standards, otherwise the data returned to the client cannot be parsed normally.
Low-power wireless technologies, such as LoRa, NB-IoT, Zigbee, etc., are specifically designed to connect low-power devices and sensors. These technologies usually involve data transfer between devices, remote monitoring and control, which is exactly the role that the HTTP protocol plays in web applications. Here are the connections between them:
Data transmission and cloud connection: Low-power devices often need to transmit the collected data to the cloud or web server for further analysis and storage. The HTTP protocol provides a standard and reliable way to achieve this data transmission.
Remote monitoring and control: Through the HTTP protocol, low-power devices can communicate remotely with the Web server, receive control instructions or upload status information to the server. This is useful in areas such as smart homes, smart cities, and industrial automation.
Data visualization and real-time feedback: Low-power devices can upload collected data to the Web server through the HTTP protocol, allowing users to view and analyze data in real time through the Web interface from anywhere. This provides a powerful tool for monitoring and decision-making.
Device registration and authentication: Through the HTTP protocol, devices can be authenticated and registered to ensure that only authorized devices can communicate with the server. This helps protect the network from unauthorized device access.
Low-power communication optimization: Since low-power devices need to minimize energy consumption, some methods can be used to optimize HTTP communication, such as using shorter HTTP requests/responses, enabling data compression, reducing the size of HTTP headers, etc. , to reduce energy consumption during communication.
The workflow of HTTP has been briefly explained before. The core is the standard of request and reply. It is also mentioned that it is an application layer protocol built on the TCP layer. So what is their detailed interaction process?
First of all, in the first step, the client needs to connect to the specified web server. When you open the browser and enter the URL to access, the browser will create a TCP client in the background and request a connection from the server. The port is the one mentioned earlier. Generally it is port 80.
In the second step, HTTP packaging is required in the background, which is the core of the HTTP protocol. What a piece of data looks like and what standards it needs to have are the essence of the protocol. For example, the following request information should contain these part
Such a piece of data will be sent to the server, and the server needs to reply to the data part after parsing the previous part. It should be noted that the server does not save the incoming data, and there is no resend mechanism, so the request failure is irreversible. , if it fails, the request needs to be reinitiated.
In the third step, the server needs to return the data. The returned data also needs to meet the HTTP protocol standards, such as the following reply data:
When the client receives the return from the server, it needs to parse the entire protocol packet according to the HTTP header. If the parsing is correct, the data part can be taken out for use. This data part can be of various types, such as the above The request type in the figure is when the device initiates a request to the server. It wants to obtain the information of the MQTT server that the device needs to connect to at this time and the three elements required for the device itself to access the mqtt server. This kind of request can also return a document in HTML format. , which is the web page file we are familiar with. When the browser receives this file and parses it, it can be displayed on the screen and become the web page we see. This kind of data can also be files, images, etc., which is equivalent to the protocol being just a carrier. , a standard carrier can carry different data types.
The last step is that HTTP is a default short link protocol. As we all know, the TCP layer is connection-oriented. However, after encapsulating it into the HTTP user layer protocol, a data request is initiated. The server returns the data. After the client parses the normal data, it needs to be disconnected. Open the connection, this is also to reduce the pressure on the server.
Finally, we need to explain HTTPS. Although HTTP is widely used, its essence is a clear text protocol. That is to say, the protocol itself has considerable security risks. Its data is easily intercepted and parsed, so HTTPS came into being. Its essence is to An encryption layer is added to the HTTP protocol to encrypt data. There are various encryption methods. Both the client and the server encrypt and decrypt the data according to the secret key required for encryption to obtain the correct data.







